The Continuous Fight Against Digital Deception
In today’s digital world, new ways of exploitation are constantly emerging. If you are not vigilant, a bad actor might just slip in right under your nose. We have seen a recent increase in a method of social engineering that some business professionals are not yet cognizant of.
Think about how your business processes new customer leads, especially those that arrive through your web site, perhaps on an information request form. You are typically more trusting, proactive, and open to engagement when someone shows interest in your services. However, be aware of how this trust can be exploited by bad actors. Scammers can easily impersonate employees or create fake business profiles that appear legitimate, pretending to be interested in your business. One of the biggest red flags when discerning scams is the sense of urgency bad actors create to make you act quickly, often without thinking. However, since you already act with urgency to convert the potential lead into new business, this red flag may not be as effective in warning you.
Imagine how easy it would be for a bad actor to send you a project proposal document that looks genuine but is infected with malware. Your eagerness to finalize the deal may lead you to bypass your better judgment and open the document, immediately exposing you and your business to significant risk.
Due diligence must be performed before interacting with anyone online. It is safer to assume ill intent than to trust blindly and risk infiltration of your systems resulting in hefty fines and the potential loss of your reputation. Bad actors will continue to invent new ways to exploit you. You must ensure your IT security strategy is growing and adapting as the threat landscape evolves.
Here are some ways you can protect your business from this type of social engineering:
1. Add CAPTCHA to your online forms: If you use forms to solicit leads, CAPTCHA is your first line of defense. It ensures that only humans can fill out the form, preventing spammers and hackers from inserting malware into your systems using high-volume methods such as scripting.
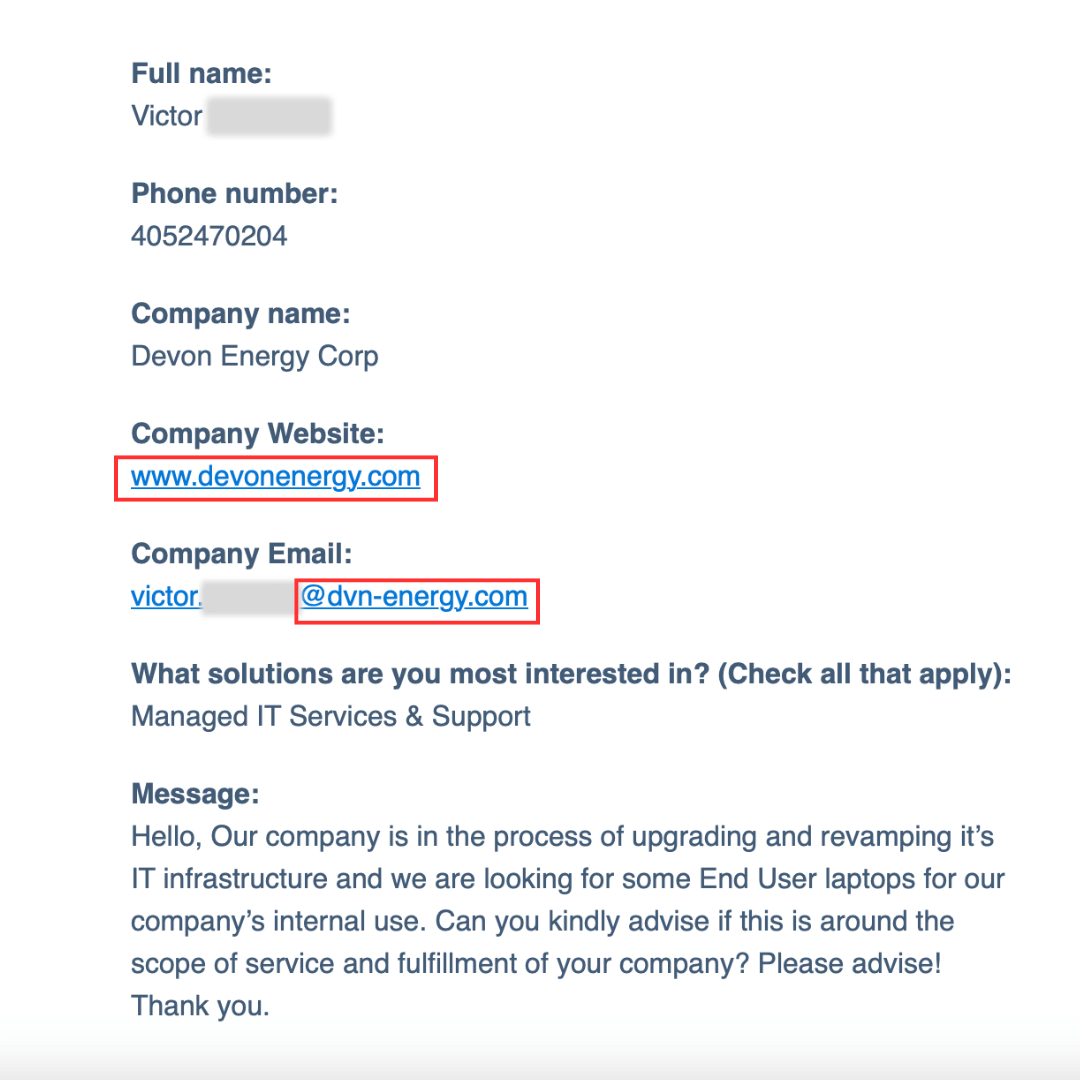
2. Compare email domains to provided website URLs: Verify that the website URL connected to the provided email matches the official website of the person. Below is an example from our CRM system that shows a discrepancy between domains.
3. Verify the form filler’s identity: Use the given first and last name to confirm that the person exists and works for the company they claim to represent. Check the official company’s website for an employee directory or use platforms like LinkedIn to verify their identity and position.
4. Hop on a call before exchanging any files: A video or a phone call is a good way to verify a potential client’s intentions. Be sure to record the meeting or call if you have that ability (remember to ask for permission). While this won’t always be possible, a reluctance to get on a phone call, or especially a video meeting is another red-flag.
By implementing these best practices, you can significantly reduce the risk of falling victim to online scams and malicious attacks. Always remain vigilant and prioritize security in every interaction. Protecting your business is not just about having the right tools, but also about cultivating a mindset of caution and diligence.
Enjoyed this blog post? Subscribe to our newsletter below and get news and IT Security best practices like these delivered straight to your inbox!

